Prioritize vulnerabilities
Port transforms vulnerability management from chaos to clarity — helping security teams focus on what truly matters to the business.
Executive summary
Port turns vulnerability management from a chaotic, reactive process into a business-first security capability. By unifying all types of vulnerabilities, enriching them with business context, and enabling API and automation-driven prioritization, Port ensures you fix what matters—fast, strategically, and sustainably.
Modern security teams face an impossible task: thousands of vulnerabilities discovered daily across code, infrastructure, cloud, and open source dependencies. Without business context, every issue appears urgent, leading to alert fatigue, wasted resources, and dangerous blind spots.
Port transforms vulnerability management from chaos to clarity — helping security teams focus on what truly matters to the business.
Port solves this by anchoring vulnerability management to business context.
Instead of starting with raw scanner data, Port starts with what matters most; your services, their owners, their environments, and their business impact.
This context powers:
- Unified visibility – All vulnerabilities from all scanners in a single platform.
- Risk-based prioritization – Focus on vulnerabilities that truly impact production and revenue.
- Automated workflows – Route issues to the right teams with the right urgency.
- Measurable outcomes – Dashboards and scorecards to track progress over time.
The result: Security teams fix the right vulnerabilities faster, while developers get actionable tickets instead of endless noise.
How it works: vulnerability ingestion flow
Port integrates with your existing security stack, automatically ingesting vulnerability data, enriching it with business context, and prioritizing it for action.
Introduction
Modern application security is complex. Vulnerabilities emerge across code, open source libraries, cloud configurations, infrastructure, and IaC—yet security teams still struggle to focus on what truly matters. Without business context, every "critical" issue looks urgent, leading to alert fatigue, resource waste, and dangerous blind spots.
Let's rethink vulnerability prioritization by designing around business context first.
Common failures in vulnerability prioritization
Many organizations fall into common traps. Here's how they go wrong—and how Port helps avoid them:
| Failing Approach | What Goes Wrong | How Port Fixes It |
|---|---|---|
| Backward (vulnerability-first) | Prioritize by CVSS, then ask what matters | Port enriches vulnerabilities with ownership, service criticality, and environment context before prioritizing |
| Severity-only (CVSS bias) | All CVSS 9.0s treated equal regardless of business impact | Port layers in service criticality, data sensitivity, and customer exposure for smarter prioritization |
| Exploit-blind | Ignores known exploited or high-risk vulnerabilities | Port lets you surface known-exploited issues (KEV, EPSS) via custom blueprint properties and automate escalation |
| Asset-blind | No owner, no context, no priority | Port’s software catalog forces mapping of services to owners, environments, and business properties |
| Siloed tooling | Multiple dashboards, inconsistent IDs, manual merging | Port ingests vulnerability alerts from scanners like Trivy, Wiz, Dependabot via integrations or custom APIs, into a unified catalog |
| One-size-fits-all | Equal SLAs for all services, unrealistic outcomes | Port enables different SLAs and triage workflows per service criticality using automations and dashboards |
| Snapshot-only | Scanning periodically misses drift | Port supports continuous ingestion (e.g., via webhook integrations) and dashboards for real-time tracking |
| Ticket-dump | Flood of generic tickets, no one fixes them | Port allows context-aware notifications and automations (e.g., escalating only high-context issues) |
| Compliance-first | Audit green, real risk remains | Port scorecards allow tracking of both compliance and actual exposure over time |
| Patch-everything-now | Teams burn out, systems break | Port’s business scoring enables prioritizing high-risk/high-impact fixes first |
Without context, teams end up chasing numbers instead of protecting what matters to the business.
The Port approach: business-first, context-driven prioritization
Port transforms vulnerability data into actionable intelligence by anchoring it directly to business context:
Unified context via software catalog
- Use blueprints, relations, and entities to represent services, ownership, criticality, environments, and compliance scope.
- Integrate with tools like Trivy, Wiz, Dependabot, Orca, Snyk, etc., to ingest vulnerabilities into Port with service links.
- Leverage API ingestion for custom tools or vulnerability sources, using Port's REST API to create/update vulnerability entities linked to services.
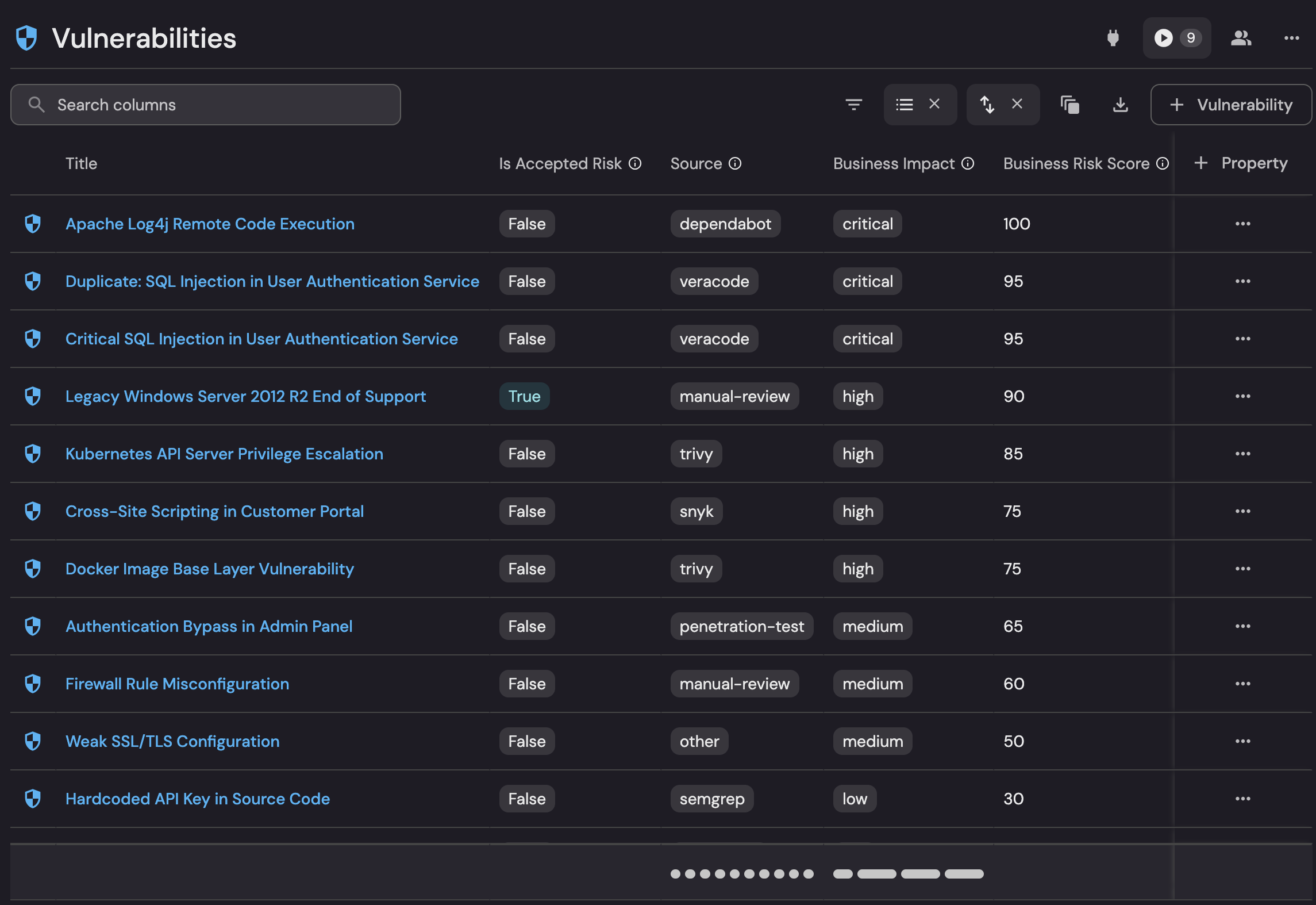
The catalog view below shows Port’s business-first approach in action: findings from many sources (Dependabot, Veracode, Trivy, Snyk, Semgrep, pen-tests, manual review) are normalized into one table and linked to services in the software catalog (e.g., User Authentication Service, Customer Portal). Catalog context—service criticality, data class, environment, ownership, dependencies—feeds the Business Impact label and rolls up into a single Business Risk Score that orders the queue (Log4j RCE at 100 down to a hard-coded key at 30).
Duplicates are collapsed, policy choices are explicit via Accepted Risk (e.g., legacy Windows 2012 R2 = True), and every row carries the metadata needed to route to the right team and meet SLAs/compliance scope. Net: Port prioritizes what matters to the business, not just raw CVEs, by unifying vulnerability data with rich catalog context into one actionable triage view.
- One view, all sources: Dependabot, Veracode, Trivy, Snyk, Semgrep, pen-tests, manual reviews—normalized into a single table.
- Catalog context applied: Each finding is tied to the service in Port’s software catalog (criticality, data class, environment, ownership, dependencies).
- Business-first scoring: Context drives Business Impact and a unified Business Risk Score that orders the queue.
- De-duped + clean: Duplicates collapsed so teams don’t chase the same issue twice.
- Explicit risk decisions: Accepted Risk captured (e.g., legacy tech), making policy tradeoffs visible.
- Right team, right SLA: Ownership and scope metadata enable fast routing and compliance alignment.
- Outcome: You work the items that matter most to the business—quickly and confidently.
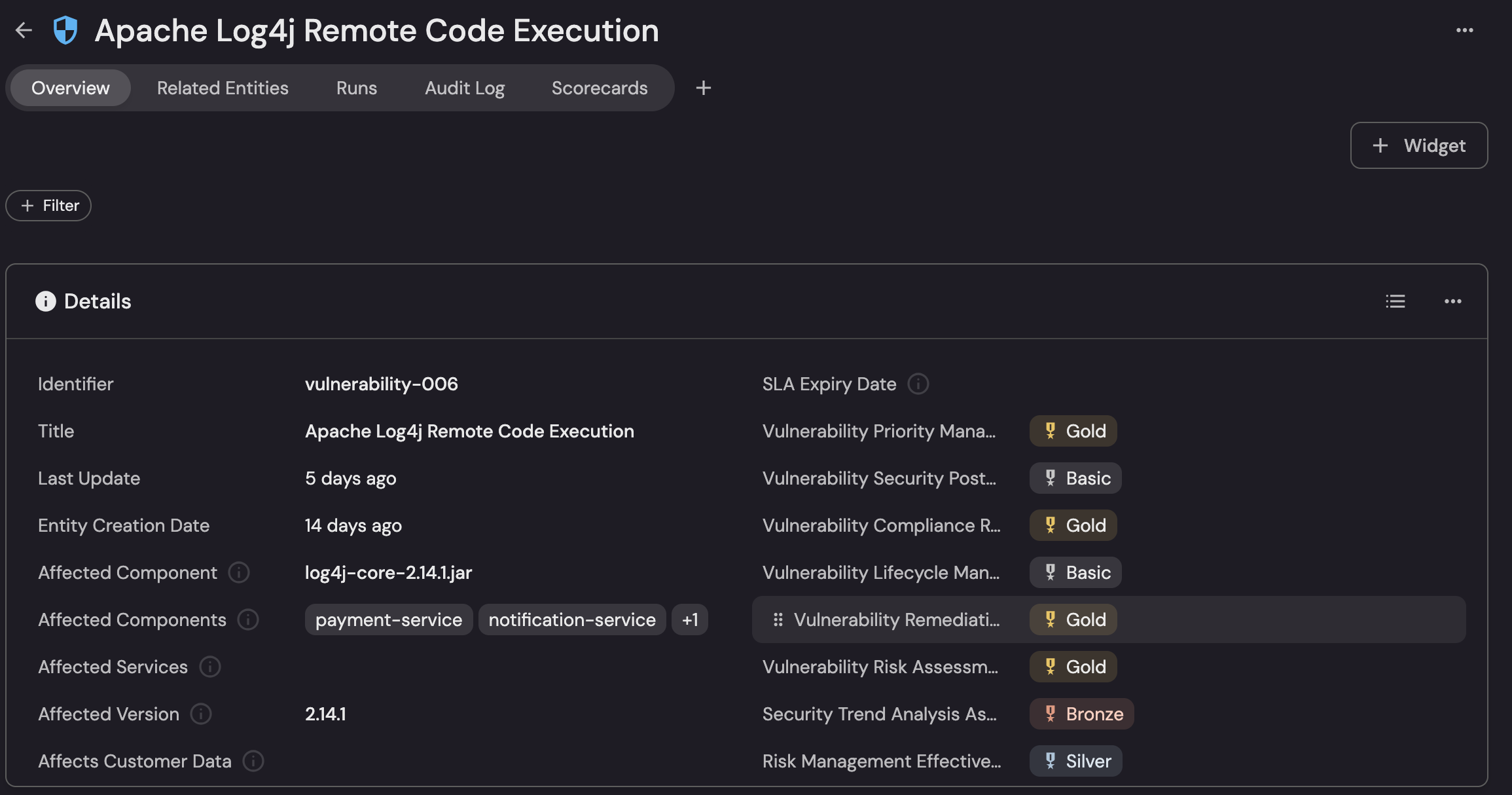
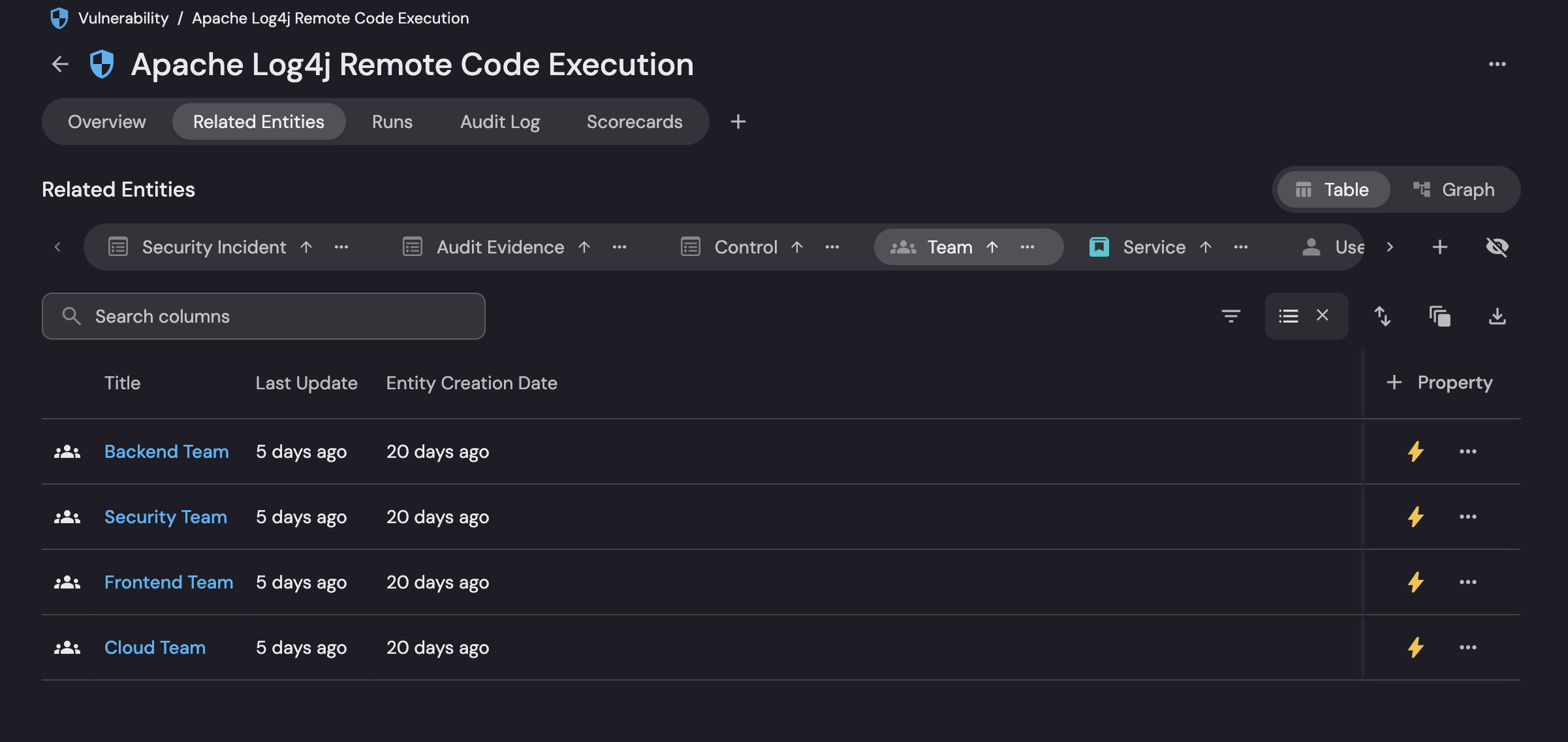
Business context enrichment
- Vulnerabilities are enriched with metadata like service ownership, environment (prod, staging), business criticality, data sensitivity, compliance implications, and recent change status.
- This enables answering: Which vulnerabilities threaten our revenue-critical production systems?
Below dashboard views show how port enriches vulnerabilities with business context—so decisions tie back to impact and ownership:
- 360° linking: Connects the vuln to incidents, audit evidence, controls, teams, services, and users in one place.
- Clear ownership & freshness: Team rows show owners and last update dates for accountable routing.
- Blast radius: Calls out affected component
log4j-core-2.14.1.jar, services (e.g., payment/notification), and version. - Customer & SLA signals: SLA expiry and Affects customer data turn technical risk into business urgency.
- Control & audit traceability: Direct links to controls, evidence, and audit log for defensible proof.
- Executive-ready scorecards: Badges (e.g., Priority = Gold, Remediation = Gold, Trend Analysis = Bronze) translate status into maturity at a glance.
- Prioritization ready: Ownership + impact + compliance + SLA context produce a business-first, fix-next call.
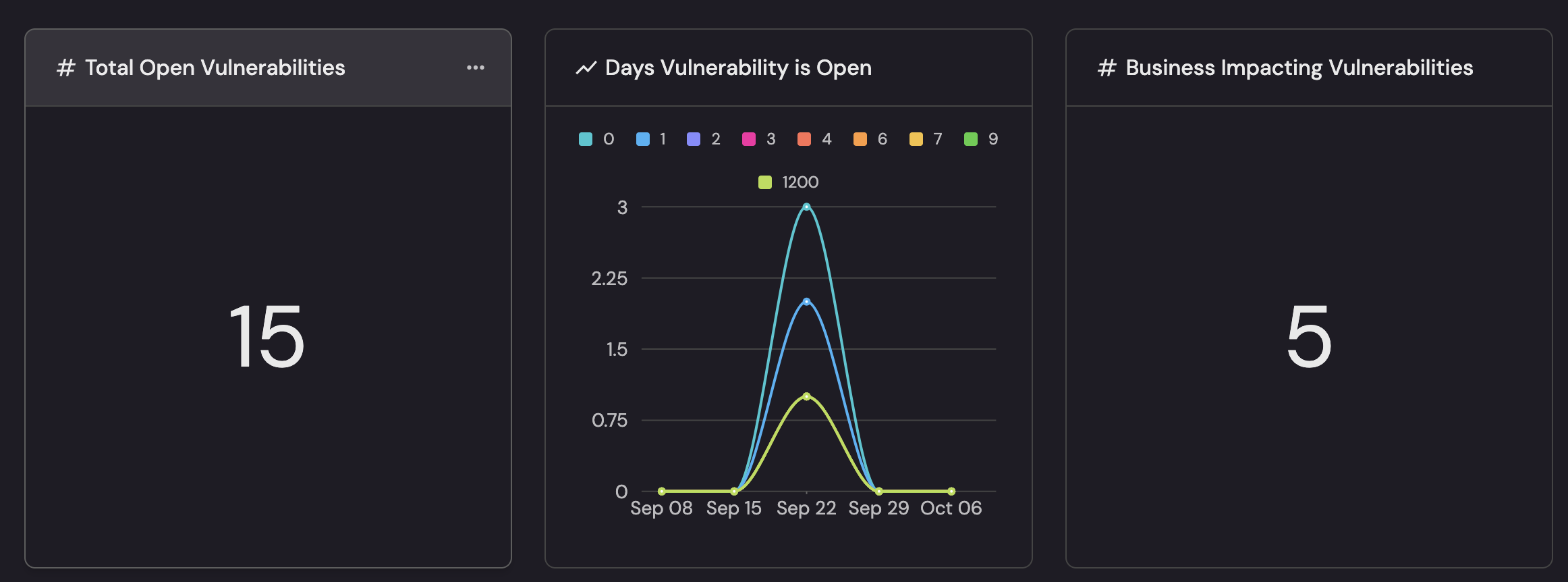
Real-time dashboards & scorecards
- Build dashboards to track vulnerabilities by severity, status, team, or service using Port's UI and widget capabilities.
- Track maturity with scorecards, showing metrics like mean time to remediation (MTTR), percentage of services with owners, or open critical vulnerabilities over time, using Port's scorecard feature.
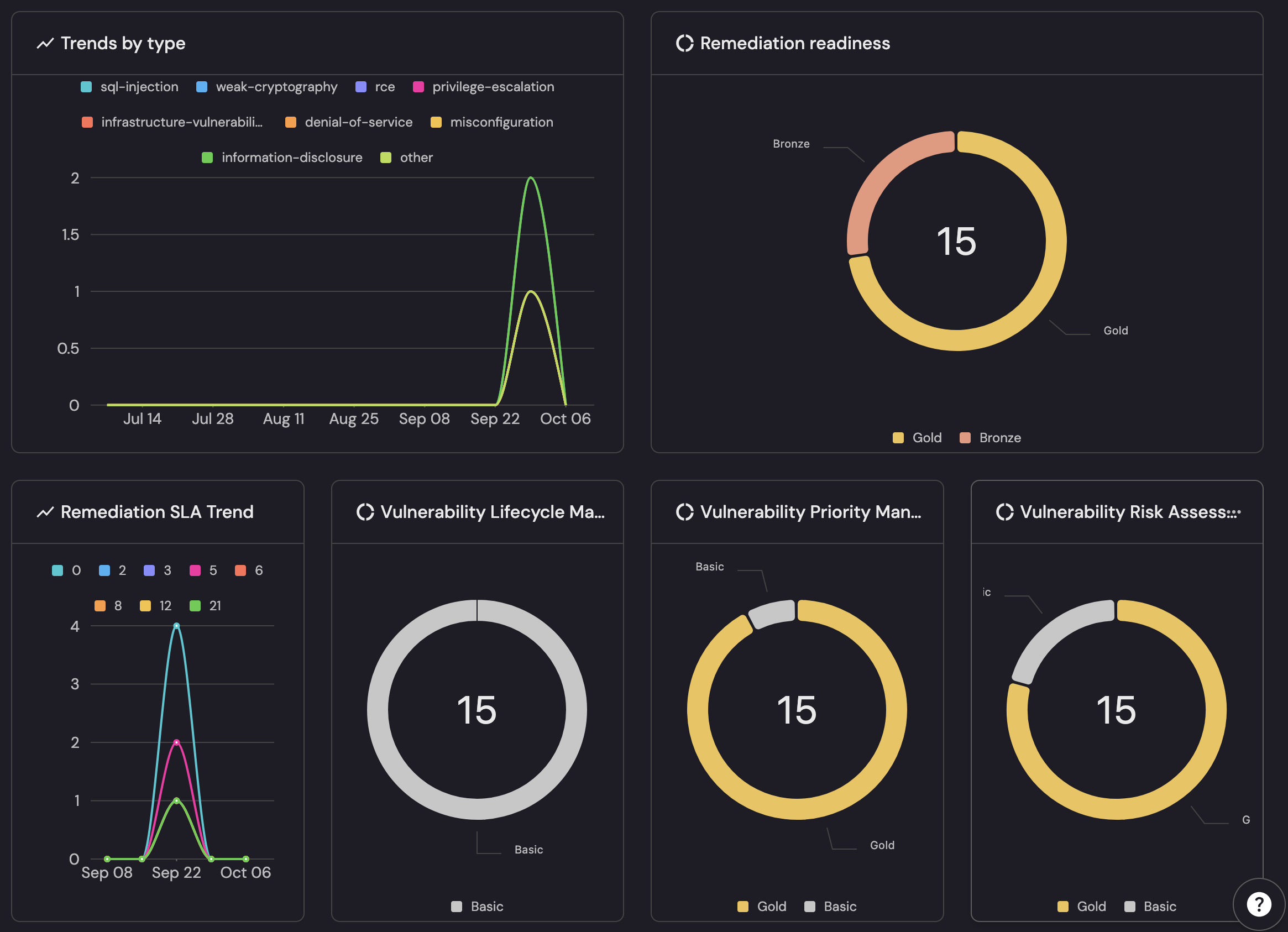
Port turns your live security data into real-time dashboards and executive scorecards. These dashboards and scorecards answer “how many, how old, how risky, and how ready” an organization is with their security capabilities. The views show current load (15 open vulns, 5 business-impacting), how long items stay open, which types are spiking, and program health with simple badges (Gold/Bronze/Basic) for readiness, prioritization, risk assessment, and lifecycle discipline.
- Live KPIs: “Total Open Vulnerabilities,” “Business-Impacting Vulnerabilities,” and “Days Open” update as scanners and tickets change.
- Trends that guide action: Type trends (e.g., misconfig vs. info disclosure) highlight surges and where to focus teams.
- SLA visibility: “Remediation SLA Trend” shows pace and potential breaches—useful for leadership and customers.
- Scorecards at a glance: Remediation Readiness, Priority Management, Risk Assessment, and Lifecycle Management surface maturity with Gold/Bronze/Basic badges—executive-readable, audit-friendly.
- Business-aware slices: Filter by service, environment, team, or customer tier from the catalog to get the exact view each stakeholder needs.
- Drill-through workflow: Jump from a metric to the underlying vulnerabilities, owners, and affected services for fast routing.
- Shareable, consistent: Common widgets keep weekly reviews, CISO reports, and auditor asks aligned to the same live truth.
Automation & context-aware workflows
- Define automations to escalate high-priority issues, such as when a vulnerability in a customer-facing prod service becomes critical.
- Build self-service actions to create tickets in Jira, Slack alerts, or trigger remediation workflows—only where business risk justifies action.
- Use Port's API and mapping layers to tailor behavior—e.g., API-driven rules, triage pipelines, or dynamic SLAs.
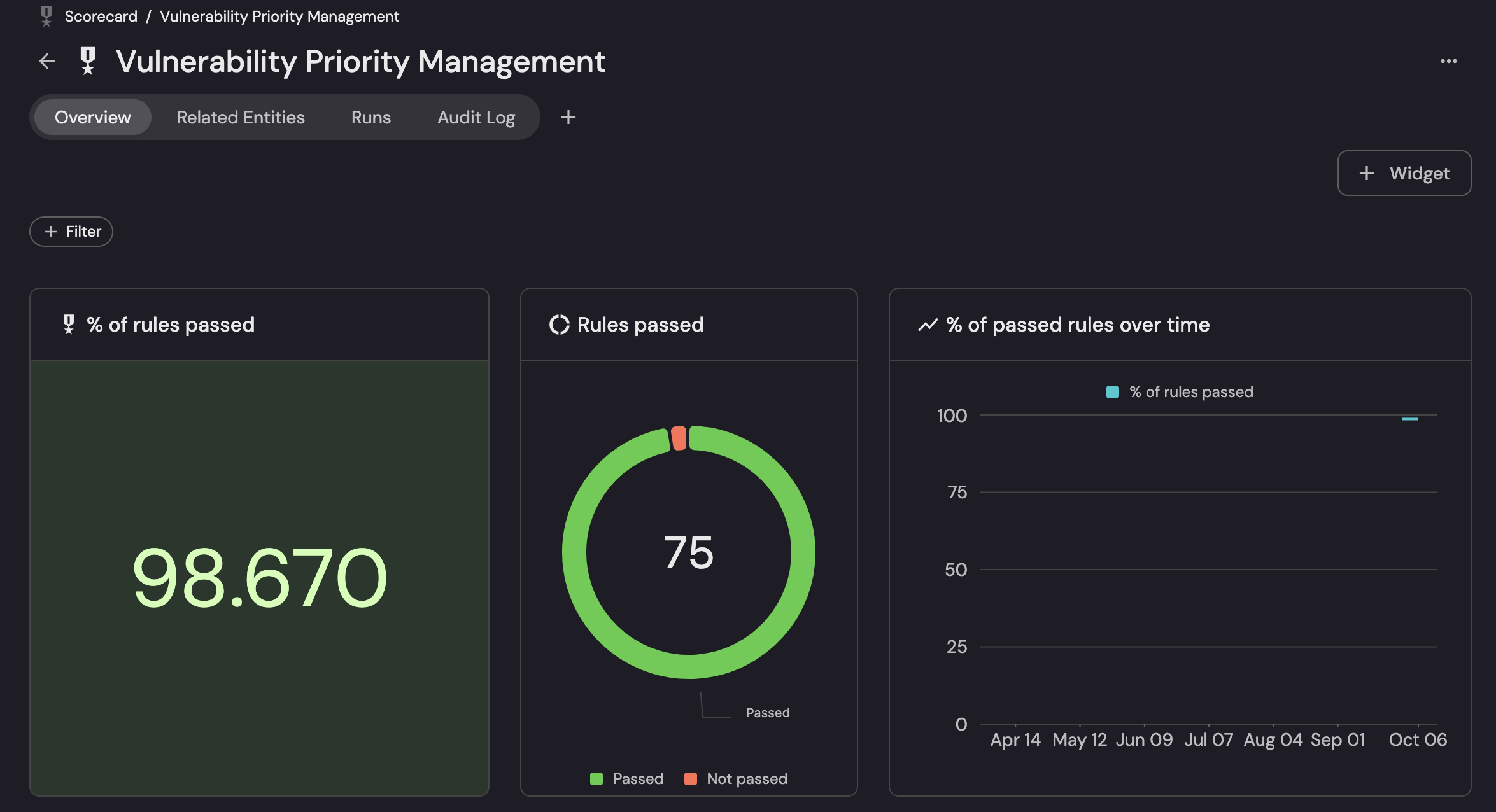
Port turns security policy into automation that reacts to context: scorecards like Vulnerability Priority Management continuously evaluate rules against the live software catalog—showing what passed (e.g., 98.67%, 75 rules) and how compliance trends over time—then trigger the right workflow when something slips.
- Policy-as-code: Rules reference service criticality, data class, SLA, env, and ownership to decide priority and action.
- Auto-evaluation: The Runs tab reflects scheduled/triggered executions on ingest, PRs, deploys, or scanner updates.
- Action on fail: Pass/fail thresholds create Jira tickets, ping Slack, open incidents, or block changes for high-risk gaps.
- Context-aware routing: Violations auto-assign to the owning team/service with links to related controls, evidence, and incidents.
- Time-series guardrails: “% of rules passed over time” exposes drift and proves continuous compliance to leadership/auditors.
- Exception handling: Waivers with expiries keep risk decisions explicit—no silent ignores.
- Audit-ready: Audit Log preserves who/what/when for every rule run and action taken.
- Reusable widgets: Drop the scorecard into any dashboard for real-time, executive-readable status.
- Example: Critical service + customer data + vulnerability > SLA ⇒
rule fails⇒Slack + Jiranotification to owner ⇒ change status to blocked until fixed.
API-driven integration & extensibility
- Port's REST API supports managing blueprints, entities, scorecards, and actions programmatically.
- Automate service metadata updates from CI/CD, incident systems, or IaC pipelines, keeping business context fresh.
Putting it into practice: a practical workflow
- Set up your software catalog with service metadata (ownership, criticality, compliance, environments) and vulnerability blueprints (e.g., Trivy, Wiz).
- Ingest vulnerabilities via native integrations or API into Port, linking them to the relevant service entities.
- Create dashboards to visualize the active threat landscape in context (e.g., “Critical findings in production, by service owner”).
- Define priority scoring combining severity with business context—for instance:
- Production service = +100.
- High revenue impact = +50.
- Customer data involved = +30.
- Known-exploited = +70.
- Automate workflows:
- Immediately notify owners when score exceeds threshold.
- Escalate top-10 findings to leadership daily.
- Create tickets and set different SLA windows based on business tier.
- Track progress with scorecards:
- Average remediation time for production-ranked vulnerabilities.
- % of services with defined ownership.
- Trend of high-risk vulnerabilities over time.
Benefits with Port
By using Port's business-context-driven approach to vulnerability prioritization, organizations achieve:
- 50%+ reduction in wasted remediation time.
- Faster MTTR on truly critical issues.
- Improved developer experience with context-aware, actionable findings.
- Better alignment between security, product, and engineering teams.
- Higher trust and accountability, backed by dashboards and scorecards.